What Does Great Cybersecurity Look Like?
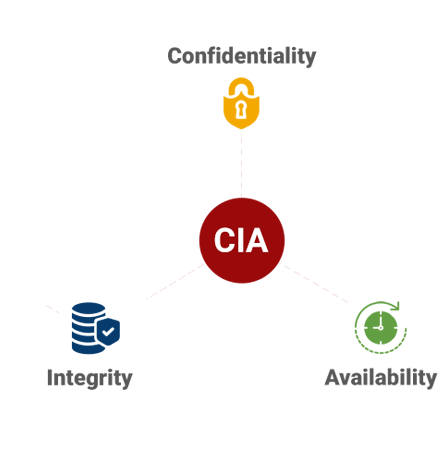
Building strong cybersecurity defenses takes thorough analysis, planning, implementation, and maintenance. Any comprehensive security strategy will satisfy each of the three aspects of the CIA triad: Confidentiality, Integrity, and Availability.
The CIA triad helps ensure that each piece of data in your company stays safe from hackers, intact and unaltered by internal and external threats, and yet remains accessible enough that peak productivity is maintained.