Managed IT Security Services for Companies That Want to Safeguard Their IT Infrastructure from Malicious Cyber Attacks
The threat of cyberattacks continues to grow year after year, especially for the relatively undefended small, midsized and enterprise businesses – organizations that have neglected to establish a full-scale robust cybersecurity solution. Unfortunately, hiring an in-house cybersecurity expert isn’t realistic. The competitive cybersecurity job market means that qualified professionals entertain competitive offers on a weekly basis. That puts building a competent cybersecurity team far outside the budget of most businesses.
The best way for companies to defend themselves against the onslaught of cybercrime is to partner with a managed security service provider (MSSP), like Kaytuso.
The fact is businesses and organizations that process any amount of credit card transactions are responsible for achieving full PCI-DSS compliance, which includes protecting cardholder data at every step of the payment process and beyond.
Flat-Rate Cybersecurity Solutions That Support Your Business Goals
A robust cybersecurity solution involves a wide range of disciplines, from perimeter defense to cloud security, mobile security, intrusion detection, malware prevention, and each more. The number of technologies and skills involved is a key reason why staffing an internal cybersecurity department is virtually impossible for most companies.
Kaytuso is a leader of the MSSP space that provides all the cybersecurity services a business needs in one tailored, flat-rate security solution. Having access to the expert team of cybersecurity professionals not only provides world-class security on a finite budget but makes sure that those protections lead to greater business agility and innovation.
Managed IT security service from Kaytuso includes the following:
Tailored security solutions custom-fit for your business
24/7 network security monitoring
Regular security audits and testing
Identity and access management
Security alerts and active response
Mobile Security
Firewall configuration
Disaster recovery and business continuity planning
Kaytuso Identify — Security Starts with a Thorough Security Assessment
To maximize the efficiency of your cyber defenses, we take a risk-based approach that starts with a thorough assessment of your organization’s risk and vulnerabilities. Once we have identified the weaknesses and exposures, we can begin designing a security roadmap for improving your cyber defenses that are tailored to your exact needs.


Identify Threats

Analyze and Rank Risks

Set Security Controls

Monitor and Review

The team at Kaytuso understands that each company must achieve a balance between security and efficiency, which is why we make sure all your systems conform to the CIA triad – an industry-standard guideline for enforcing security that never overshadows overall productivity.
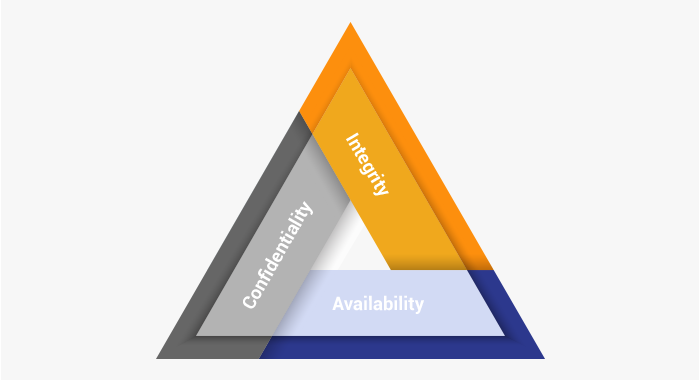
Securing company assets by granting permission on a need to know basis.
Ensuring data is not tampered with during storage or transmission.
Providing consistent access to data and services, including backup and disaster recovery plans that ensure data is protected.
Kaytuso: Comply+ Deep Regulatory Compliance Expertise
Regulatory compliance is a leading concern for organizations in industries like financial services, healthcare, and retail where sensitive personal data is critical to operations. In recent years, these industries have experienced a rapid expansion in their regulatory compliance requirements and now face higher penalties for compliance failure than in the past.
Enlisting the help of the compliance experts at Kaytuso will help you clarify your organization’s compliance requirements and ensure they’re consistently met, freeing your internal team from a major burden and enabling a new level of focus in your organization.
We have over 20 years of experience deploying regulatory compliance solutions at companies including:
- Hospitals and clinics
- Doctors and dentist offices
- Research institutes
- Accounting and law firms
- Banks and financial advisory firms
- Private equity and brokerage firms
Our regulatory compliance expertise includes:
- HIPAA
- PCI-DSS
- FINRA/SEC
- DFAR & NIST SP 800 - 171
- NYS-DFS Part 500
Kaytuso: Fortify — Complete and Holistic security built on best practices and tailored to your needs.
The NIST Cybersecurity Framework
Cybersecurity frameworks are collections of tools and best practices that provide a guideline for building strong cyber defenses. The National Institute for Standards and Technology (NIST) framework is one of the most comprehensive security frameworks available and has been widely adopted in both government and private sector organizations.
We’re strong proponents of the NIST framework and have been using it for years to optimize our client’s cybersecurity protections. There are five core principles of the NIST framework.

Identify
Gain full visibility of your physical and digital assets, and their vulnerabilities
Protect
Control access to those assets with appropriate safeguards
Detect
Possess visibility over your network and identify threats quickly
Respond
Contain cybersecurity events with a response plan and clear lines of communication
Recover
Effectively recover any damaged services with clear action points
Want to learn more about how the NIST framework helps us defend our clients?
Malware Protection
Hundreds of millions of new malware variants are hitting the Internet every year To minimize the chances of being infected, you’ll need a vigilant, proactive, and timely response. Managed security services from Kaytuso include sophisticated, up-to-date solutions to help organizations protect themselves from these threats.
Ransomware
While ransomware may have peaked in 2017, it’s still the leading cyber threat facing SMBs. Projections from Cybersecurity Ventures shows that ransomware will cost businesses $11.5 billion a year for the near future. To stay secure, you’ll need to keep your protections updated and ahead of the latest trends in cybercrime.
Vulnerability and Penetration Testing
When was the last time you tested your network security? Any change in your network infrastructure or software can create unintended vulnerabilities, which is why it’s important that even small businesses perform regular testing of their cyber defenses. High-profile organizations in targeted industries like healthcare and finance should test with even greater frequency.
Vulnerability Scanning
Vulnerability scanning uses automated tools to gauge the security of your network. Regular vulnerability scans can tell you a great deal about your security and help you identify subtle weaknesses that human analysts might miss on their own. This process involves checking for network misconfigurations, weak passwords, poorly configured proxy servers, as well as performing a detailed analysis of how the traffic on your network moves.
Uses remote protocols like secure shell (SSH) and remote desk protocol (RDP) to scan the interior of your network
Searches only the public-facing aspects of your network infrastructure
Penetration Testing
Penetration testing is a more comprehensive test in which humans simulate a real hacking attempt on your company network. Penetration testing uses all the same tools that real-world hackers would use to gain access to your data like phishing, social engineering, and application back-doors, making it an effective barometer of your organization’s real-world cybersecurity preparedness.
Employee Training
Statistics show that employee error is responsible for the most data loss incidents per year. Even though the majority of these events are unintentional, the fact remains that your staff is on the front line of your cybersecurity effort whether they know it or not That makes it imperative that your team is armed with the latest information and best practices for maintaining data security.
Phishing Protection Starts with Informed Staff
Phishing is the most common way for hackers to invade your network. By disguising emails or text messages as a reputable business or trusted individual, phishing attacks try to obtain valuable company information, like network credentials, passwords, or financial information. Research shows that a vigilant program for training employees can significantly over the rate at which they open phishing emails.
A Cybersecurity Partner Who's Trusted Across the Country
Kaytuso is a recognized leader in the managed security services field. Based in New York City, it provides clients around the country with powerful cybersecurity strategies and cutting-edge solutions that optimize their defenses and minimize the chance of disaster.
We’re passionate about bringing our long-standing expertise to help businesses in need and are eager to answer your questions. To talk with one of our cybersecurity experts, or for more information about our cybersecurity services, please call us at 212-792-9932 or contact us at .

 Get Started
Get Started
